SecOps Platform
Harpy Defence delivers a fully managed, end-to-end Security Operations (SecOps) platform designed to equip security teams with a complete, ready-to-deploy infrastructure. This full-stack solution captures, normalizes, and correlates security data from every layer of your digital ecosystem—empowering your organization to detect threats faster, respond more effectively, and make data-driven security decisions.
Built for modern enterprises, the Harpy Defence SecOps platform seamlessly integrates threat intelligence, automated workflows, SOC operations, and real-time alerting into a unified environment. From ingestion to action, every component is optimized to reduce operational overhead and increase visibility across your infrastructure.
At Harpy Defence, we recognize the importance of your security data. You shouldn't have to settle for limited visibility—gain full-spectrum insight across your infrastructure, including endpoints, cloud platforms, SaaS tools, internal networks, and perimeter defenses.
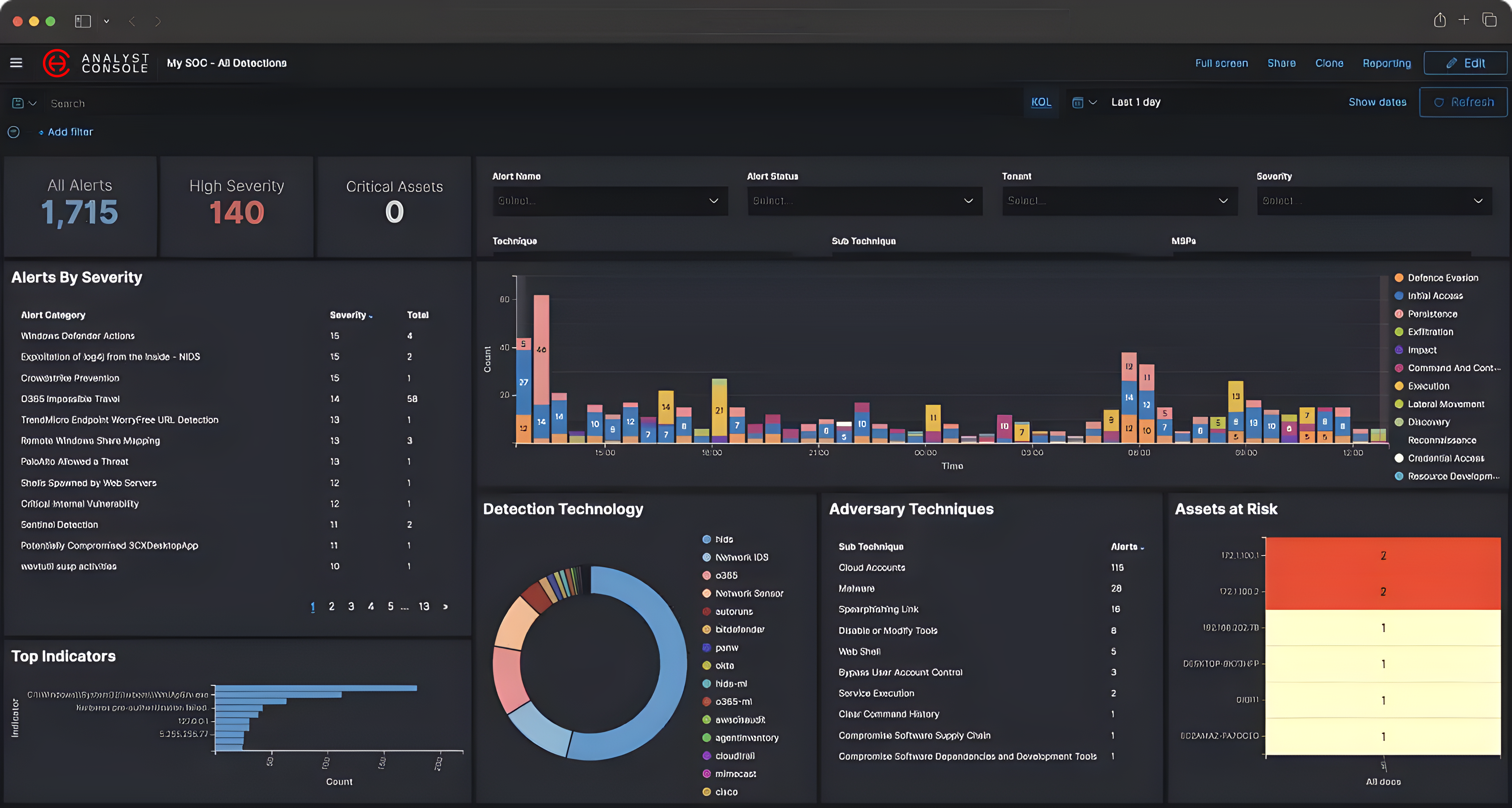
Key Capabilities Include:
- Plug-and-play deployment for rapid onboarding and minimal disruption
- Automated correlation and enrichment of security data from endpoints, networks, cloud workloads, SaaS tools, and more
- Integrated threat intelligence to enhance context and prioritize critical alerts
- Real-time alerting and incident response workflows to ensure swift mitigation
- Customizable reporting and executive dashboards for both technical teams and business leadership
- Scalable architecture capable of supporting growing infrastructure and complex environments
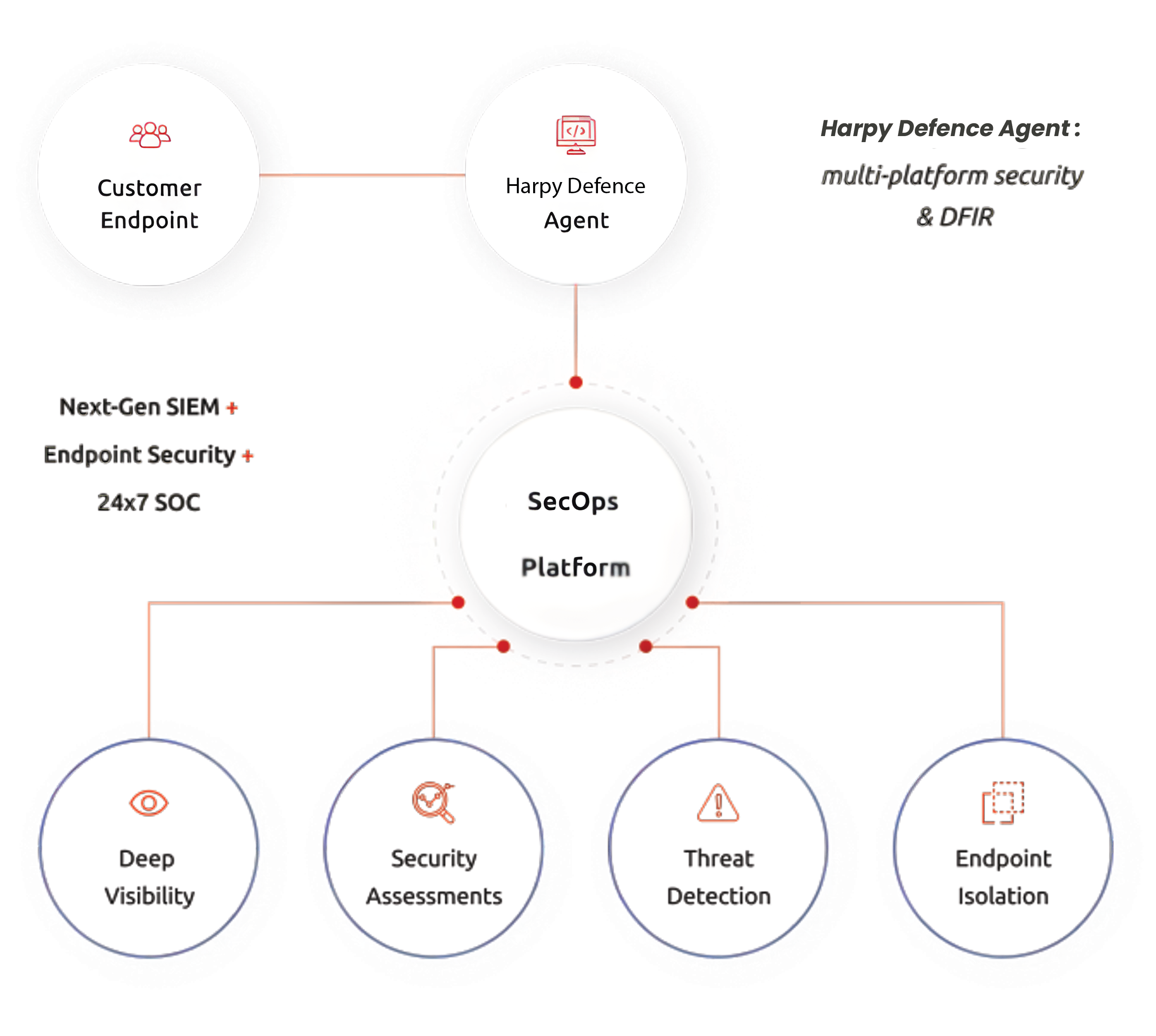
Endpoint Threat Detection and DFIR
The HarpyDefence Agent provides seamless visibility into your endpoints. Easily deployable with just a few clicks, the agent quickly starts sending endpoint logs from your clients' devices to our cloud platform for advanced threat monitoring and response.
Complete Cloud Coverage
Achieve full visibility and threat detection across your O365, Azure, AWS, and GCP environments. Our cloud monitoring service offers ongoing assurance and proactive cyber risk management, uncovering vulnerabilities and misconfigurations within your cloud environment.
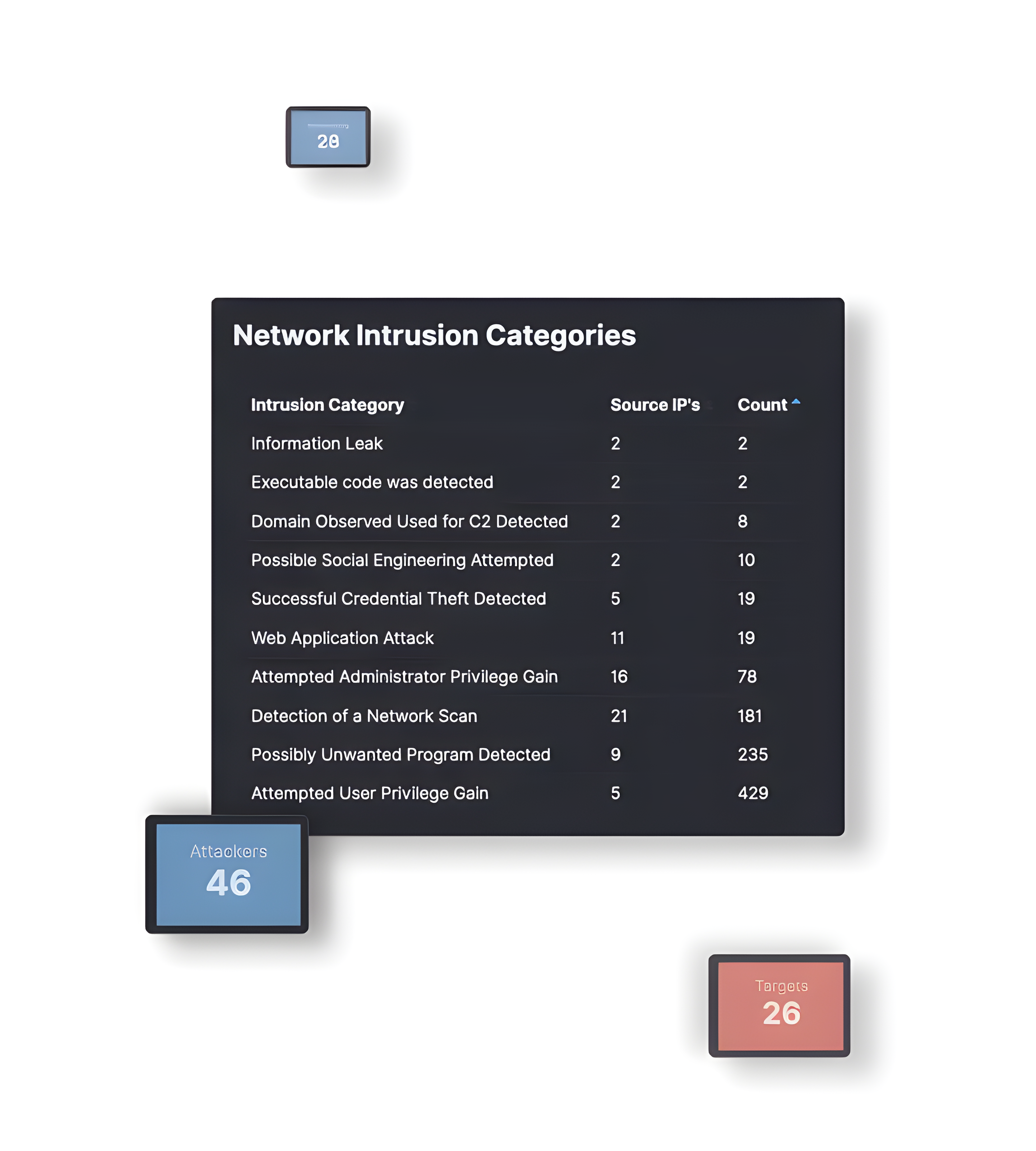
Outsmart Hackers with NDR and Deception
Detect lateral movement and receive precise, high-quality alerts with our Network Detection and Response sensors and deception technologies. Convert noise into actionable data, track every action taken by attackers, and respond promptly with confidence.
Comprehensive Feature Set
Here’s an all-inclusive overview of the capabilities we offer:
- Complete SecOps Suite (SIEM, XDR, NDR, TI, Automation)
- SaaS Delivery Model
- Ongoing Platform Management
- Detection Use Cases - Daily Updates
- Machine Learning and User Behavior Analytics
- Curated Threat Intelligence
- SIEM and 24x7 SOC services
- SOC Workflows for Alerting and Escalations
- Real-Time Dashboards
- Customizable Reports
- 24x7 Incident Response
- Threat Hunting Artefacts
- MITRE ATT&CK Mapping
- Playbooks and Automation
- Digital Forensics Toolset
- Network Detection and Response
- Vulnerability Management
- Cloud Monitoring and Assurance
- Inventory and Security Configuration Benchmarking
- Attack Surface Management
- Log Management and Data Retention
- Compliance Reporting
- Customer Portal with Real-Time Reports
- Hacker Deception
Documented Evidence – The Core of High-Quality SOC and Incident
All activity is continuously logged and available for real-time inspection at any scale, delivering deep, forensic-level visibility to support breach detection, live forensics, and effective incident response.
| Attack Type | BEST EDR PRODUCTS | Other EDR Products | SIEM/SOC | Visibility + SecOps |
|---|---|---|---|---|
| Common threats (malware) | 100% | 70% | 100% | 100% |
| Sophisticated breaches | 10% | 0% | 30% | 100% |
| Zero day Attacks | 0% | 0% | 20% | 100% |
| Account takeovers | 0% | 0% | 50% | 100% |
| Incident Response and Investigation | 10% | 0% | 30% | 100% |
| Supply Chain Attacks | 10% | 0% | 20% | 100% |